Demystifying JA3: One Handshake at a Time
Recently, I was browsing a website with BurpSuite and found out that the website was blocking my requests. In the pursuit of unlocking the mystery of how I have stumbled across an incredible TLS fingerprinting technique called JA3.
Backdrop
Fingerprinting clients and blocking them based on a particular set of rules is not new. Many companies do have intelligent ways of Fingerprinting clients(one reason being to detect bots and malicious traffic) by using a cookie to track a user uniquely. After Snowden’s leak back in 2013, many websites started to adopt the HTTPS version by default. Many applications like malware, IoT devices also use TLS to connect securely to the Server. Thus, the popularity and widespread of the TLS protocol led to research and discovery of newer ways to fingerprint users uniquely.
How do HTTPS Connections work?
HTTPS in short is combination of two things:
- TCP(Transmission Control Protocol) — 3 Way Handshake
- TLS (Transport Layer Security)Client — Server Negotiation
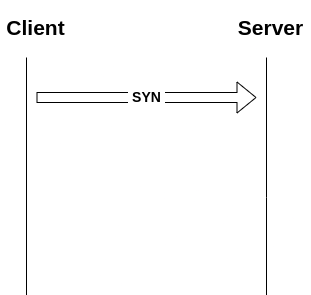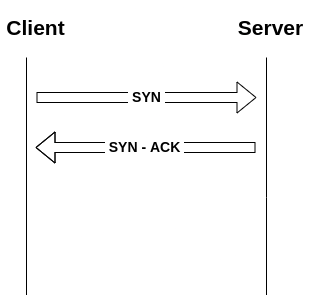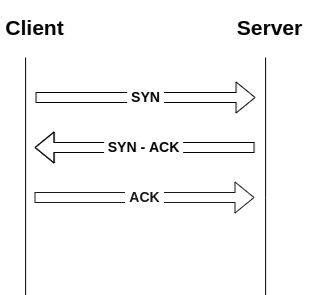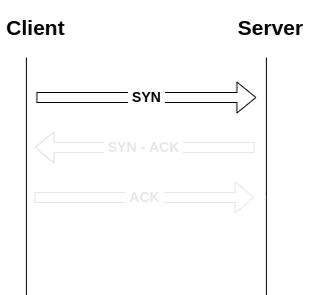
TCP Handshake, also known as a 3 Way handshake, is a process in which the Client and Server establish a TCP Session. The following diagram illustrates how a TCP Connection is established.